Case study
Secure Access Service Edge for the Enterprise (SASE) construction project
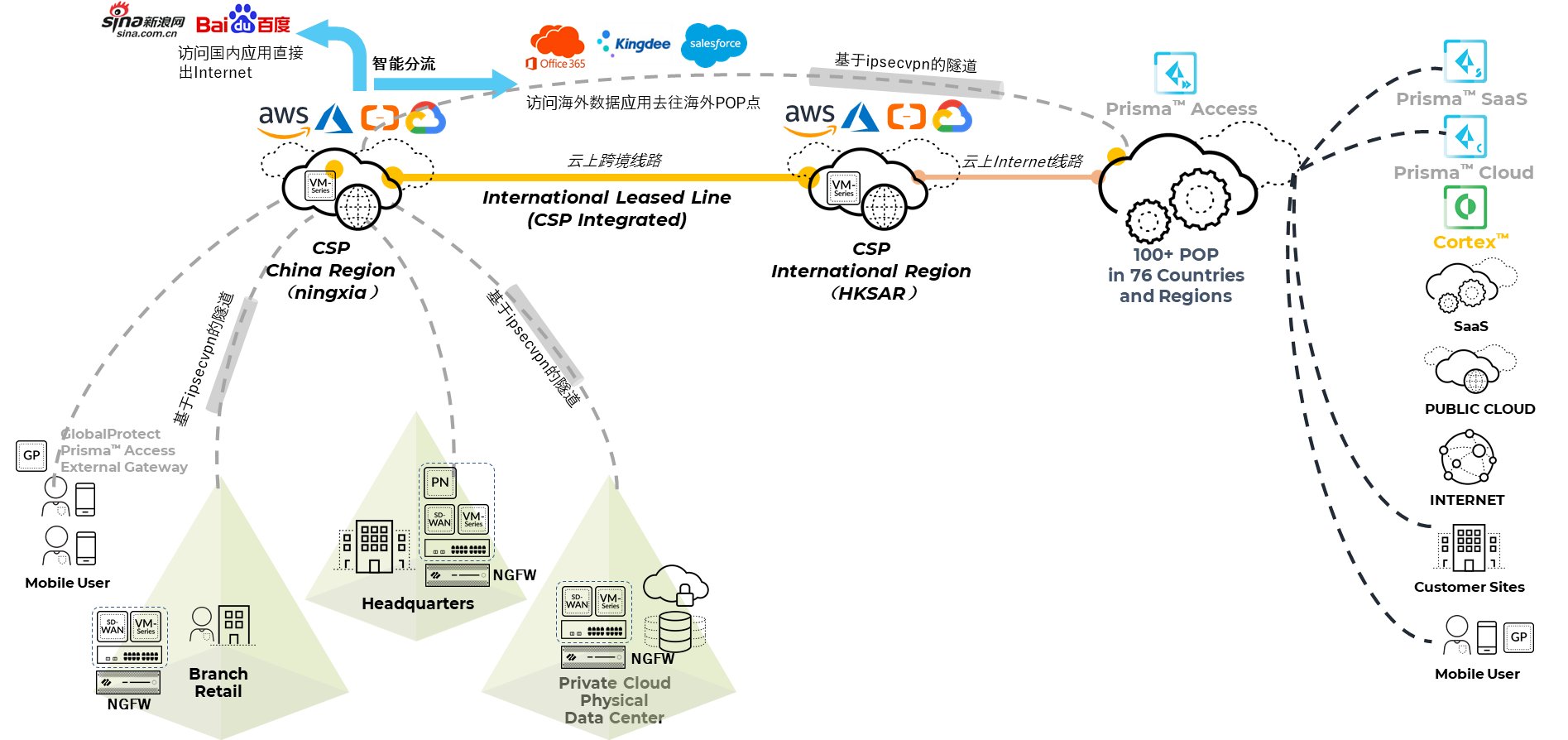
The adoption of cloud technology and increased customer mobility has revolutionized the way network and security infrastructure is built. The emerging SASE model integrates network and security in the cloud, breaking through the limitations of the traditional architecture. As applications are increasingly delivered in the cloud and telecommuting becomes the norm, organizations will have to re-examine the way they deploy networks and security. To connect and secure organizations now and in the future, networks and security must be integrated into the cloud.
Enterprises are actively deploying applications across data centers, public clouds, and edge locations for use by employees at home, at work, or in remote locations. These highly distributed environments drive the need for secure connectivity, and the top priority for enterprise networks is to ensure a tightly integrated network and security solution. Enables enterprises to meet this need by providing tightly integrated and comprehensive security access services edge solutions that combine security, network, and digital experience management.
SASE integrates network and security functions into a single cloud service, simplifying enterprise IT architectures and eliminating the need for multiple vendors and hardware devices, reducing complexity and cost. This simplified architecture reduces the administrative burden on IT teams and improves management efficiency.
SASE provides comprehensive security measures, including encryption, multi-factor authentication, threat protection and data leakage prevention, to ensure the security of enterprise networks and data. Its zero-trust approach enhances security by authenticating users, devices, and applications, no longer relying solely on IP addresses or network locations. This security framework can better meet the challenges of network security and protect enterprises from potential security threats.


